
How Good OSINT Makes Penetration Tests More Effective
Every great pentest starts with good OSINT. When public exposure is understood early, testing becomes faster, more precise, and more representative of attacker behavior.

OSINT Discovery for Credit Unions Case Study
A case study on how a single GitHub leak exposed 23 credit unions and financial institutions revealing a shared supply chain security risk.

Manufacturing Penetration Testing in Delaware
At Exploit Strike, we specialize in securing manufacturing environments by assessing IT infrastructure, operational technology (OT), and physical security on the factory floor. Learn more about how and our case study from a Fortune 500 Automotive Manufacturer.

The Buildup to a Successful Penetration Test
Penetration testing success starts in the pre-engagement phase, where goals, scope, and boundaries are defined to ensure an ethical, effective, and compliant assessment. Learn how Exploit Strike handles this well with precision and integrity.

Understanding Persistence Techniques in Penetration Testing
Understanding persistence techniques is essential for both attackers and defenders. While penetration testers use them to evaluate security postures, blue teams must recognize and mitigate these risks to maintain system integrity.

Can you be a good pentester without knowing how to code?
Can you become a good pentester without knowing how to code? Let’s hear what our followers on LinkedIn had to say about this.

Post-Penetration Testing Excellence
Penetration testing is a critical step in assessing and improving your organization's cybersecurity posture. Learn more with this free download.
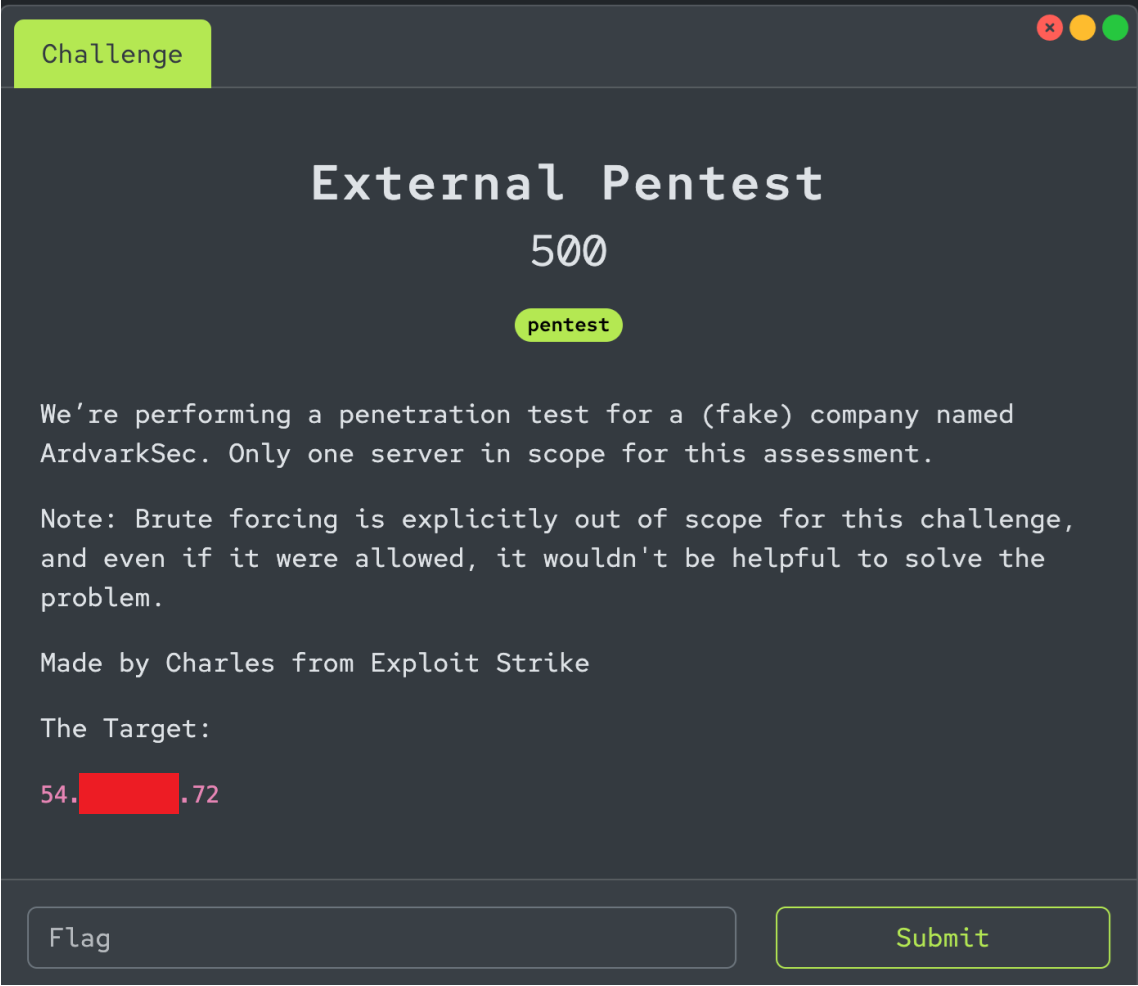
Secure Delaware CTF: External Pentest Writeup
Walkthrough of the external pentest CTF problem that was presented at Secure DE 2024.

Pentesting in Delaware
Exploit Strike is your preferred partner for Penetration Testing in Delaware from Wilmington, Newark, Middletown, Smyrna, Dover, down towards Georgetown, Rehoboth, Lewes, Seaford, and Selbyville.
