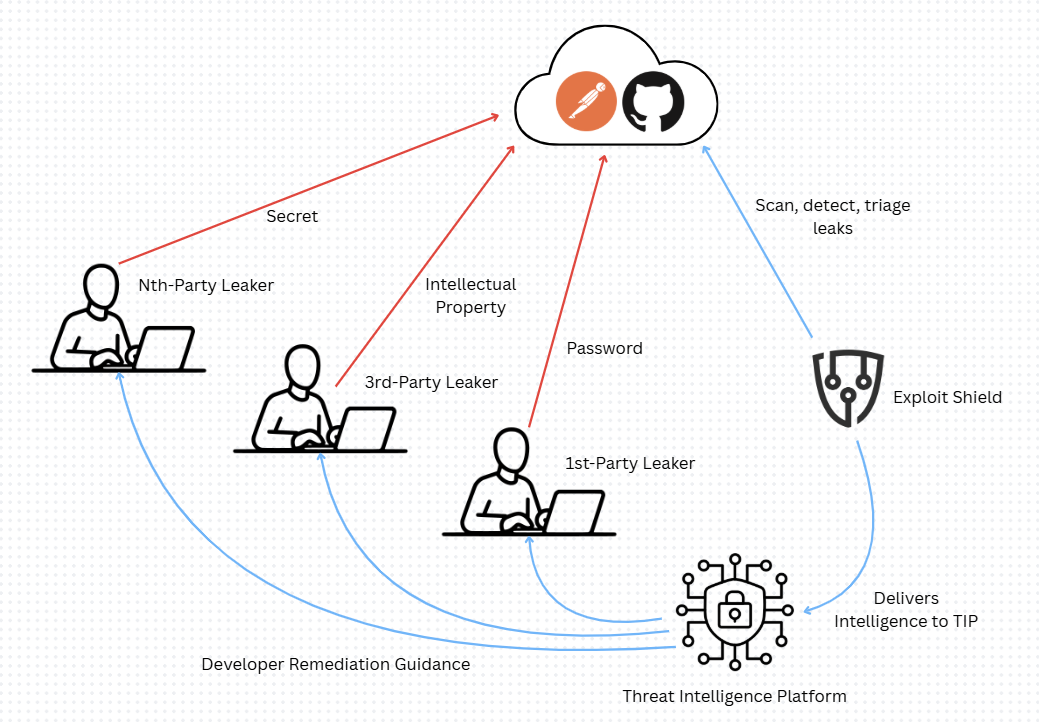
We hunt for leaks in the developer ecosystem outside of your perimeter.
WELCOME TO EXPLOIT SHIELD
Exploit Shield hunts for publicly exposed credentials, tokens, and other first- and third-party leaks on clear web developer ecosystems.

Where We Monitor
Exploit Shield continuously monitors high-risk public developer ecosystems
GitHub
Public repositories and commit history are continuously scanned for exposed secrets, hardcoded credentials, infrastructure configuration files, OAuth keys, and internal documentation.
Postman
Public workspaces, collections, and environments are analyzed for API keys, bearer tokens, authentication headers, environment variables, and internal system references that could expose production services.
Discovery
Triage
Exploit Shield continuously monitors public developer platforms like GitHub and Postman to identify exposed credentials, keys, and sensitive infrastructure data.
Discovery
Exploit Shield continuously monitors public developer platforms like GitHub and Postman to identify exposed credentials, keys, and sensitive infrastructure data.
Actionable Threat Intelligence
FINDINGS INCLUDE A SUMMARY OF THE LEAK, INVENTORY OF ARTIFACTS, LEAK ATTRIBUTION

Case Studies
HOW EXPLOIT SHIELD ENABLED TEAMS TO PREVENT MASSIVE BREACHES
Gateway to Mass Exposure
A single public personal GitHub repository contained production configuration files for 23 credit unions and banks. Exposed artifacts included:
- Core banking URLs (Symitar, Fiserv DNA)
- Visa and Mastercard integration credentials
- Institution-specific production secrets
The repository was public from May 2022 to February 2025. None of the affected parties detected it.
Enterprise API Ecosystem Exposure
An employee moved private Postman collections to a personal account and made them public. Exposed artifacts included:
- Hundreds of API credentials
- Production and non-production secrets
- Authentication tokens actively in use
The exposure persisted for over a year before disclosure. The organization was unaware.
The 20-Year Admin Repository
While using Exploit Shield for OSINT recon for a penetration test, we discovered a public personal GitHub repository containing:
- 20 years of internal sysadmin notes
- Plaintext domain administrator credentials
- Service account passwords
The repository was not malicious. It was a trusted employee preserving personal notes before leaving the company.
Where Exploit Shield Sits
EDR sees endpoints.
Pentesting sees authorized systems.
ASM sees perimeter infrastructure.
Exploit Shield hunts leaks on public developer platforms.
When secrets leak outside your environment, we detect them, structure the evidence, and feed it into your existing workflows.

Built to Feed the Systems You Already Use
Integrations
Exploit Shield is not another dashboard your team has to monitor. Findings are structured and delivered directly into the systems your security and IT teams already operate.
Jira
Splunk
OpenCTI (STIX 2.1 compatible)
Additional SIEM, TIP, and workflow integrations are available upon request. Exploit Shield is API-driven and designed to integrate into mature security environments.